Bridge Firewall - Opnsense Bridge Firewall Stealth Invisible Protection Aziz Ozbek
A transparent firewall acts more as a tap on a line while a routing firewall. When you configure Sophos Firewall in bridge mode it forwards packets such as Spanning Tree Protocol STP Rapid Spanning Tree Protocol RSTP and multicast routing.
Opnsense Bridge Firewall Stealth Invisible Protection Aziz Ozbek
Firewalld provides a dynamically managed firewall with support for networkfirewall zones that define the trust level of network connections or interfaces.
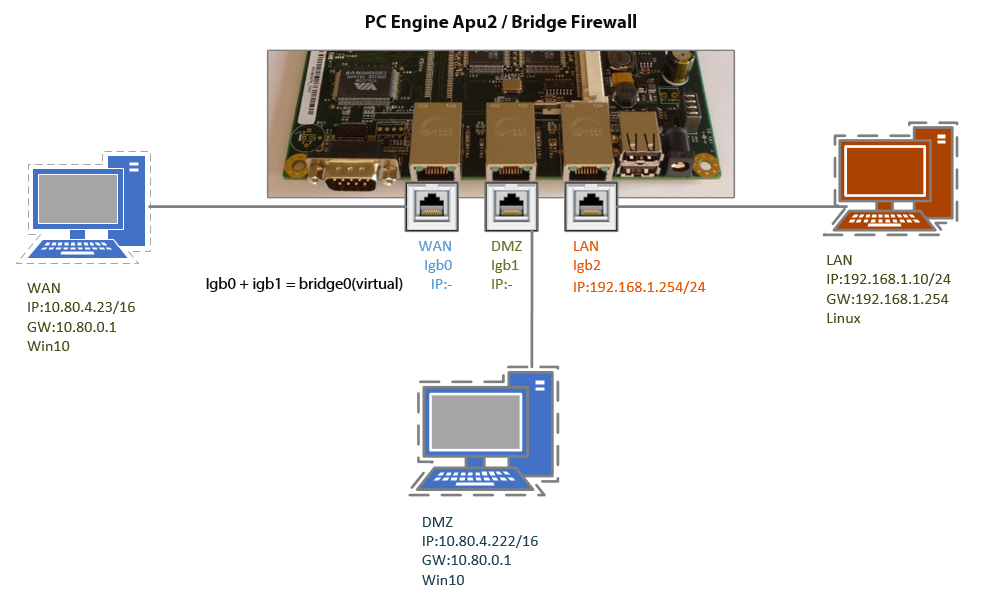
Bridge firewall. Bridge firewall iptables. If you change your firewall to a bridge firewall your firewall will filter the MAC addresses like a. A transparent firewall also known as a bridge firewall is a Layer 2 application that installs easily into an existing network without modifying the Internet Protocol IP address.
Built on an infrustructure of Dell Servers Cisco switches Cisco PIX firewall Linux proxy server Windows 2003 Server with Active Directory. The transparent firewall is not a routed hop but instead acts as a bridge by inspecting and moving network frames between interfaces. There is a separation of runtime and permanent configuration options.
A routing firewall participates in the IP process whereas a bridging or transparent firewall does not. Data in transit to and from Bridge is encrypted. CBP officers retrieved 13 packages of cocaine concealed within the firewall of the vehicle seizing a total of 3073 pounds of cocaine worth an estimated 23698000.
We support High Availability HA on bridge interfaces when you deploy Sophos Firewall in bridge mode using the assistant. Bridging and firewalling Filtering with bridged interfaces functions similar to routed interfaces but there are some configuration choices to alter exactly how the filtering behaves. Bridge runs in the background by seamlessly encrypting and decrypting messages as they enter and leave your computer.
The bridge feature allows the interconnection of hosts connected to separate LANs using EoIP geographically distributed networks can be bridged as well if any kind of IP network interconnection exists between them as if they were attached to a single LAN. Cisco Firewall Technologies See all courses Williams public profile badge. Managed a large network of 14 locations 1000 pcs.
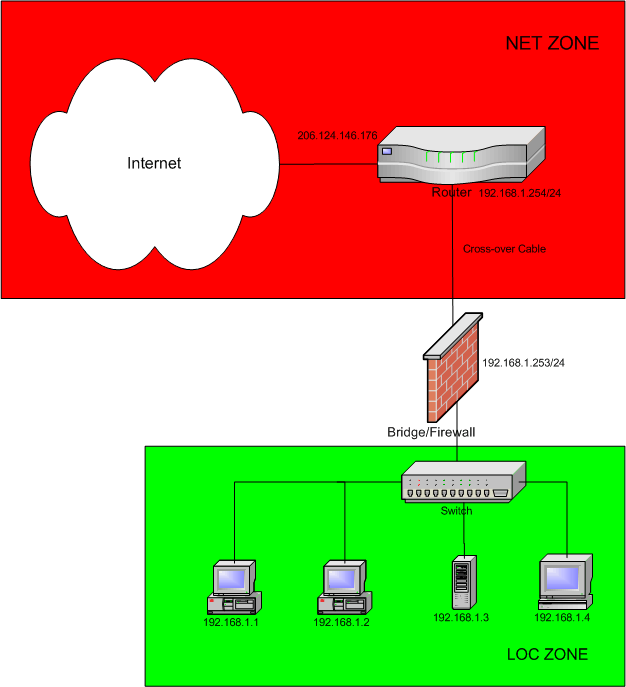
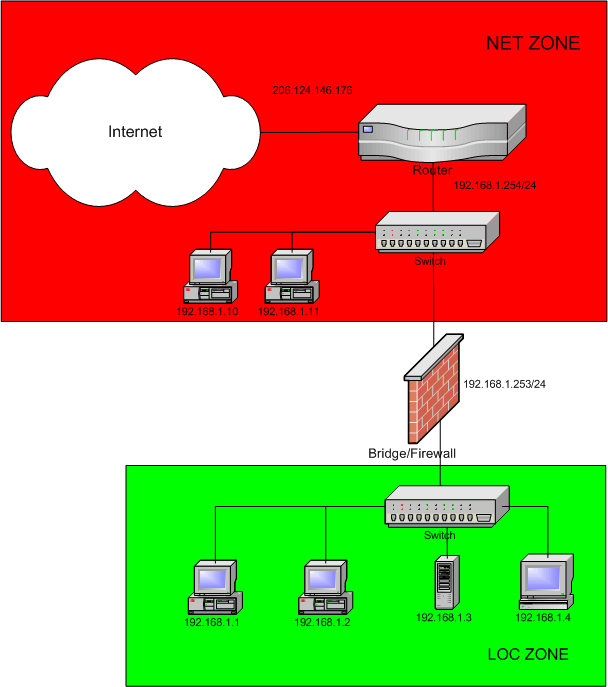
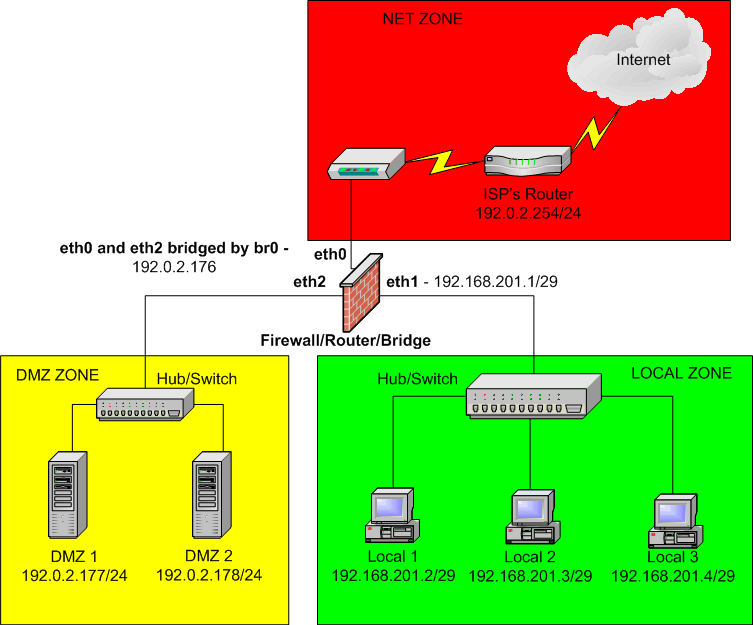
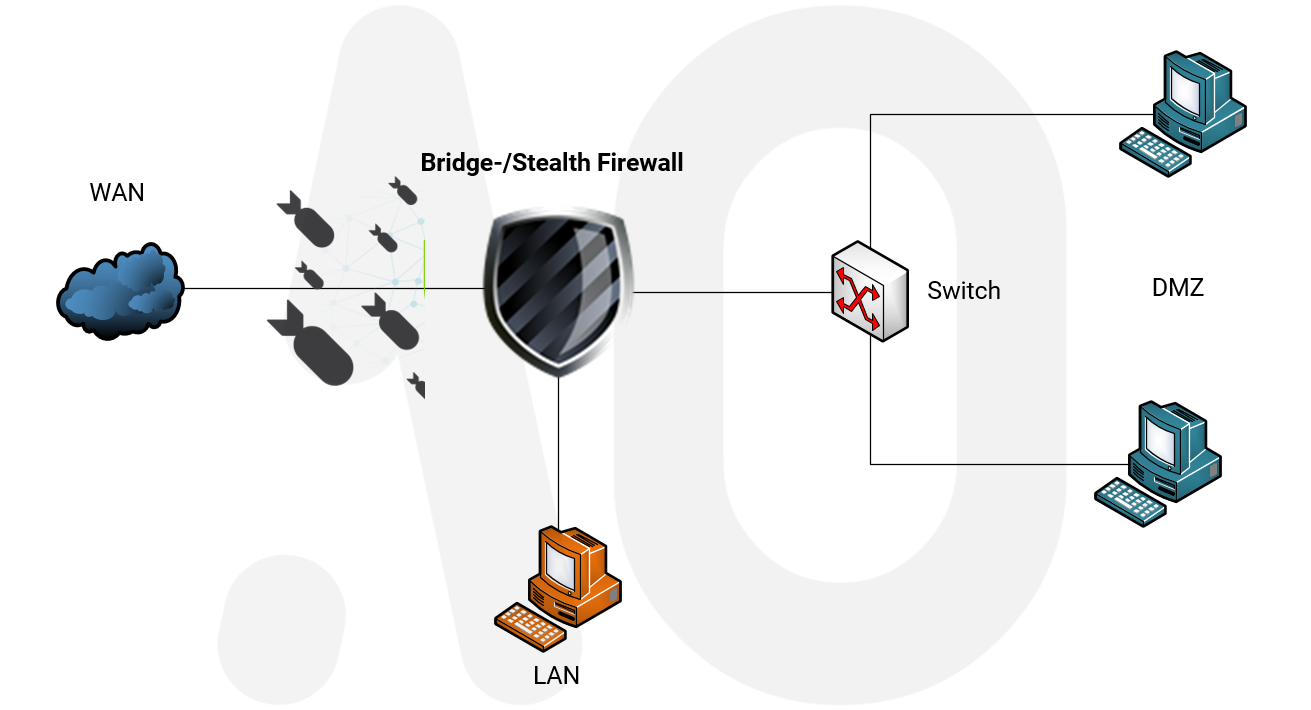
A bridge providing NAT and firewall capabilities The first configuration uses the bridge as a firewall with network address translation NAT that protects a server and internal LAN clients. The firewalls if not configured work on the third network to seventh application OSI layer. The Shorewall system the BridgeFirewall has only a single IP address even though it has two Ethernet interfaces.
If firewalld is active on the host libvirt will attempt to place the bridge interface of a libvirt virtual network into the firewalld zone named libvirt thus making all guest-host traffic on that network subject to the rules of the libvirt zone. 562 others named William Graves are on LinkedIn. It has support for IPv4 IPv6 firewall settings ethernet bridges and IP sets.
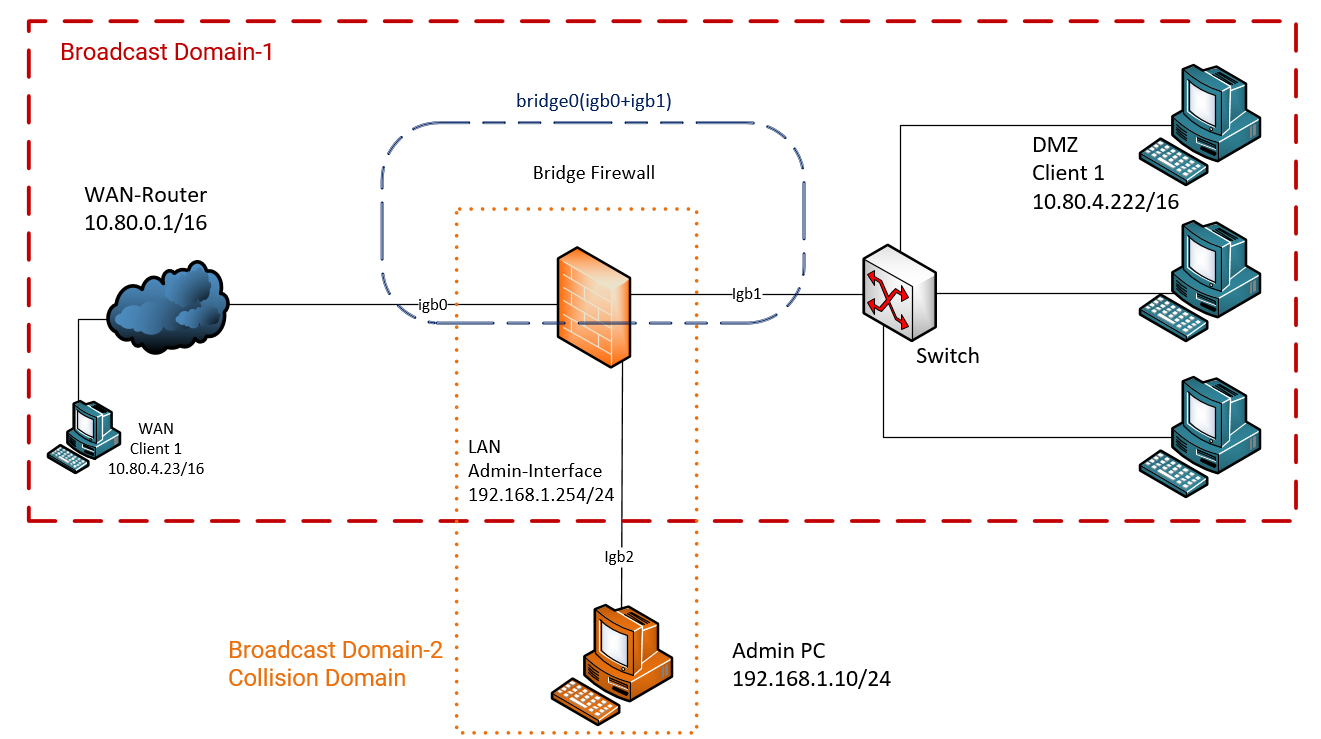
The app is compatible with most email clients supporting IMAP and SMTP protocols. The driver a 25-year-old woman from Piedras Negras was turned over to Homeland Security Investigations special agents for further investigations. A desktop computer is connected to bridge port eth0 A web server with SSH for remote administrador is connected to bridge port eth1.
The bridge feature allows the interconnection of hosts connected to separate LANs using EoIP geographically distributed networks can be bridged as well if any kind of IP network interconnection exists between them as if they were attached to a single LAN. The IP address is configured on. All communication is initiated from behind the on-premises firewall and therefore does not require you to manage additional exceptions.
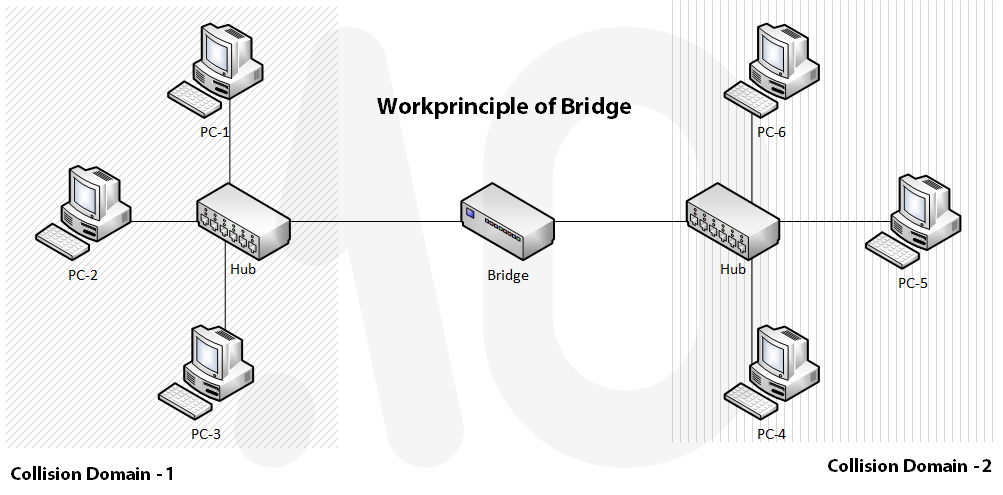
That being said I attempted to replicate Francois setup in my environment but was struggling to get Bridge firewall to work. Bridge Firewall Bug In order to leverage NSX-T Bridge Firewall you must be utilizing the Edge Bridge Profiles. But a bridge firewall uses targeted forwarding of network packets on the second Data Link OSI layer.
After the FDB decision packets can follow either the input or the forward. Subscribe to the LIVE. Tableau Bridge applies the following security designs.
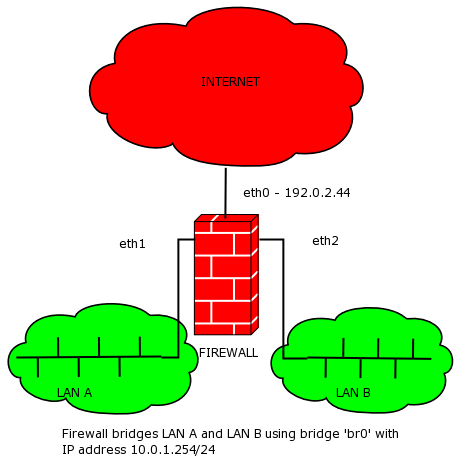
Assuming a bridge with two ports eth0 and eth1. In other words a router connects two networks together and translates between them. The following example shows how to deploy a stateful bridge firewall this assumes the bridge interface has no IP address.
BRIDGE Brand Coordinator San Angelo TX. A diagram of the network configuration is shown below. Help with installing configuring and using the ProtonMail bridge can.
Why might you want to. A bridge is like a patch cable connecting two portions of one network together. A bridging firewall acts as a bridge but also filters the packets it passes while remaining unseen by either side.
By default firewall rules are applied on each member interface of the bridge on.
Transparent Bridge Firewall With Seperate Management Port Netgate Forum

Deploy Sophos Firewall In Bridge Mode

Unsichtbarer Schutz Mit Linux Firewall Auf Bridge Ebene
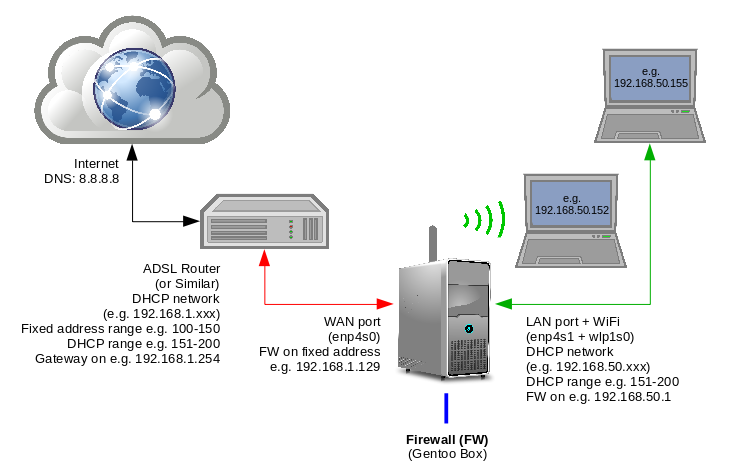
Ethernet Plus Wifi Bridge Router And Firewall Gentoo Wiki

A Transparent Firewall Using Openbsd Bin Blog
Opnsense Bridge Firewall Stealth Invisible Protection Aziz Ozbek
Redundant Firewalling On Openbsd Bridging Mode

Opnsense Bridge Firewall Stealth Invisible Protection Aziz Ozbek
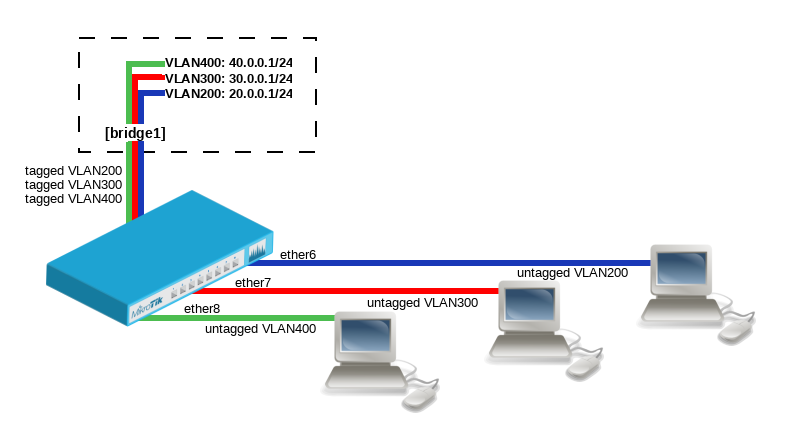
Manual Interface Bridge Mikrotik Wiki

Sophos Firewall In Bridge Mode Techbast
Opnsense Bridge Firewall Stealth Invisible Protection Aziz Ozbek

Quick Review Of Firewall Connectivity Options Routed Mode And Transparent Mode Alexandre M S P Moraes